Even messaging applications like WhatsApp use encryption protocols to protect messages. The same happens with information between you and your bank. The process of encrypting data is known as cryptography. Cryptography is the art of securing messages to prevent unauthorized access. There are two main types: symmetric and non-symmetric cryptography.
Symmetric cryptography involves using a shared key to lock and unlock messages. People have used this method for centuries, but there is still a tiny chance of someone breaking the encryption. Non-symmetric cryptography is more complex than the previous one. It uses a public key to lock the message and a private key to unlock it. Even if someone intercepts the message, it remains secure without the private key.
One example of non-symmetric cryptography is the RSA protocol, which uses a large number that is difficult to factor in. However, quantum algorithms like Shor’s algorithm could disrupt these protocols.
Many discussions revolve around the potential threat quantum computing poses, which could break existing encryption methods. However, it is imperative to recognize that there is no cause for alarm. As new technologies have emerged, encryption has faced challenges throughout history, only to be met with innovative and more secure solutions. In today’s article, we will discuss how quantum computing could address these worries and propose new solutions, which have already been tested in real hardware.
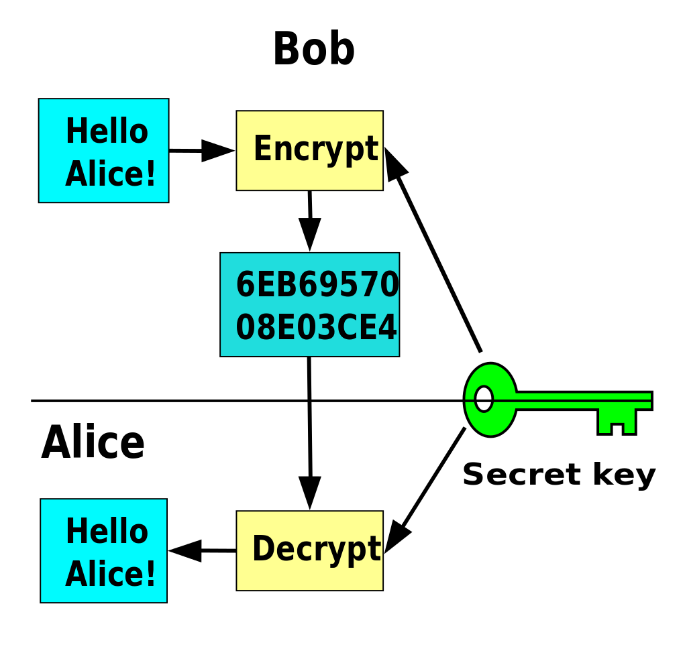
Symmetric-key cryptography. © Wikimedia commons.
Safeguarding Cybersecurity in the Age of Quantum Computers
As we mentioned, quantum computers pose potential cybersecurity challenges. Still, two key areas offer solutions: quantum cryptography and post-quantum cryptography.
Quantum cryptography leverages the capabilities of quantum computers to address cybersecurity risks. For instance, Quantum Key Distribution (QKD) employs quantum principles to secure communication channels, ensuring the confidentiality and integrity of data transmission, even in the presence of quantum attacks.
Post-quantum cryptography focuses on developing new classical algorithms that can withstand quantum attacks. Postquantum cryptography ensures the long-term security of sensitive information by creating algorithms resistant to the computational power of quantum computers.
The National Institute of Standards and Technology (NIST) in America is actively developing a program for Post-Quantum Cryptography Standardization. This program aims to establish standardized encryption algorithms that can resist the threats posed by quantum computing. By fostering collaboration and research, NIST is leading the way in preparing for the era of quantum computers and ensuring robust cybersecurity measures for businesses.

NIST logo. © NIST.
Top Companies
MagiQ Technologies is a pioneering quantum encryption company based in Massachusetts, USA. They offer the MagiQ QPN, a market-leading Quantum Cryptography solution that provides unrivaled network security. This advanced product offers a foolproof defense against various cryptographic key distribution challenges.
The technology behind MagiQ QPN works on the principles of quantum mechanics. By transmitting critical bits at the single photon level, one photon at a time, the information encoded on each photon becomes irreversibly altered if observed by an unauthorized party. This method establishes a quantum channel that instantly detects any attempted eavesdropping. The security of the key exchange is guaranteed, as the keys cannot be intercepted without modification, making it impervious to future advances in algorithms and others.
Among other companies, we can also find PQShield, an expert in post-quantum cryptography specializing in transitioning to upcoming public-key cryptography standards. The company was founded in the UK in 2018 as an Oxford University spin-out. It offers a comprehensive range of products and solutions that allow organizations to protect their digital assets against future threats.
PQShield’s product portfolio includes the PQPlatform, cryptographic software development kits (SDKs), and encryption solutions for messaging platforms and applications. Their offerings cover post-quantum and classical cryptographic primitives. What sets PQShield apart is its active involvement in developing the NIST post-quantum cryptography standardization process.
Hardware development
Researchers are exploring various physical platforms in the quest for a fully operational quantum computer. Among these platforms, technologies utilizing arrays of neutral atoms controlled by light beams show great potential and scalability. The flexibility in controlling atomic configurations allows for different atomic graph constructions.

Researchers recently conducted Rydberg-atom experiments on integer factorization in a recent collaboration between the Korea Advanced Institute of Science and Technology (KAIST) and PASQAL1. Remember that the computational difficulty of factoring large integers, which is difficult for humans and machines, is the base of the RSA protocol. The researchers successfully factorized small numbers, demonstrating the practical application of the Rydberg atom in quantum cryptography. While challenges remain for large-scale implementation, these findings also glimpse a future where quantum computing revolutionizes our approach to solving complex mathematical problems.
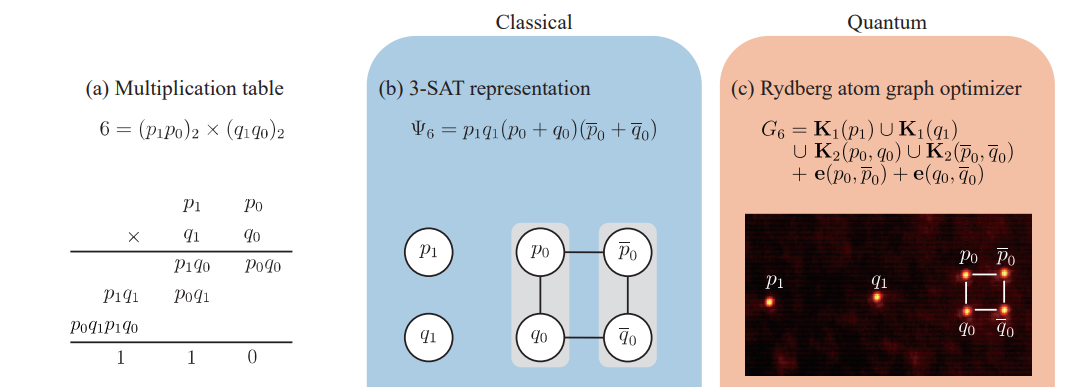
Process to program the integer factorization problem with the Rydberg-atom graph for 6=p x q. We can see the associated multiplication table, and the Implementation of Rydberg atom quantum computer. © PASQAL.
Conclusions
Quantum cryptography and post-quantum cryptography offer solutions to ensure robust cybersecurity measures, and many companies are at the forefront of developing quantum encryption and post-quantum cryptography solutions. It is crucial to stay proactive in preparing for the era of quantum computers and ensuring the long-term security of sensitive information.
The advent of quantum computing challenges existing encryption methods and offers a unique opportunity for people and businesses to innovate in their cybersecurity strategies. Future leaders should consider the advantages of quantum-resistant technologies and partnering with companies specializing in quantum and post-quantum cryptography solutions. This proactive approach safeguards sensitive information.
Moreover, the rise of quantum computing emphasizes the importance of cybersecurity literacy and awareness at all levels of an organization. Training and educating employees about quantum threats and the principles of quantum-safe practices will be vital.
Additionally, engaging in dialogues and collaborations with cybersecurity experts and industry consortia can provide valuable insights and access to the latest developments in quantum-resistant technologies. This collaborative and informed approach will be vital to navigating the complex cybersecurity landscape in the age of quantum computing, ensuring business continuity, and protecting against emerging threats.
- Park, J., Jeong, S., Kim, M., Kim, K., Byun, A., Vignoli, L., Henry, L.-P., Henriet, L., & Ahn, J. (2023, December). A Rydberg-atom approach to the integer factorization problem. arXiv. [2312.08703] [quant-ph]. https://arxiv.org/abs/2312.08703 ↩︎
